- ... Linux1.1
- and more exactly : it runs in Linux. It's
a kernel patch
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... POST1.2
- Power On Self Test. Auto-test of different
physical components of the computer : chips, processor(s), memory, etc.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... medium1.3
-
This is an often forgotten vulnerability. You must be sure that the
computer can't boot on another medium (disk, cd-rom) than the one you
wanted, for example by using the correct BIOS parameters, or by removing
the floppy driver.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... loaders1.4
- Don't forget
to put a password to lilo!
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
boot1.5
- We suppose that the boot loader, the kernel and the init
process are not compromised. If we prove that they can't be
compromised while the box is working, we prove by induction that they won't be
compromised for every future boot sequence. The initial point where
these part are not compromised is the moment after the securisation of
the box and before its first working day.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... interactions1.6
- We can't
elimate them as the major part makes the whole job of the box :
serving web pages, firewalling, ...
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... execute''1.7
- And not ``who init must not execute''
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
ACL1.8
- Access Control Lists
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... partial1.9
-
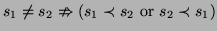
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... element1.10
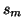 is minimal
is minimal
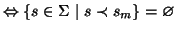
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... capabilities2.1
- Please see linux/include/linux/capability.h for a complete and up to date
description of these capabilities
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... LFS2.2
- LIDS-free session. See chapter
![[*]](/usr/share/latex2html/icons/crossref.png)
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
relation3.1
-
An equivalence relation must verify
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
master6.1
- See LIDS_LFS_MASTER in section
![[*]](/usr/share/latex2html/icons/crossref.png)
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...DNA8.1
- Direct Network Access : code used for LIDS to access network directly from the kernel, without any user space code support, to send mails or logs to remote syslog daemons.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... thread8.2
- a process that is
created by the kernel, and that run in kernel space
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... value9.1
- an empty set for EMPTY_SET, a full set for FULL_SET, and the corresponding bit
to 1 for any other
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... ones9.2
- ie the closest parent which is a NODE in lids.conf
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... correct9.3
- maybe using vrfy
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... sequence9.4
- See the BOOT_TIME option in section
![[*]](/usr/share/latex2html/icons/crossref.png) .
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
IP10.1
- in hexadecimal format. For example, 127.0.0.1 will be 0100007f
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
![[*]](/usr/share/latex2html/icons/crossref.png) ">...
IP10.
">...
IP10.![[*]](/usr/share/latex2html/icons/crossref.png)
-
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... twice10.1
- This
permit lidsadm to encode the password once internally before
sending it to the kernel, so that an interception out of lidsadm does
not reveal it.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... DNA12.1
- Direct Network Access : code used for LIDS to access network directly from the kernel, without any user space code support, to send mails or logs to remote syslog daemons.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... code12.2
- ask also for its message queue size
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... trust12.3
- if not, the password field must be given as a compilation time option, as it used to be before
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...parent16.1
- parent is current
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... tags16.2
- i.e. lids_caps_s with a positive tag field
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...LIDS_OUTLAW16.3
- the access is granted regardless of the
permissions. See section
![[*]](/usr/share/latex2html/icons/crossref.png)
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.